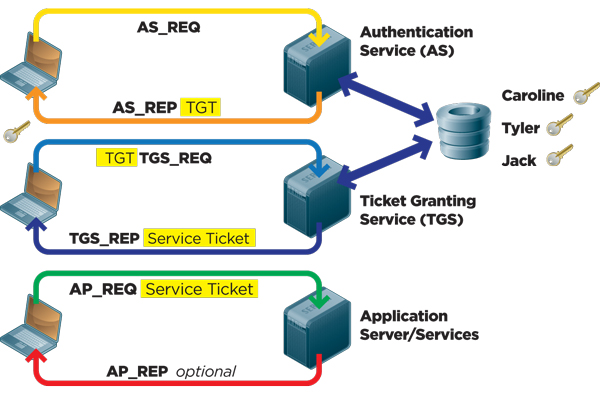
Kerberos Authentication / How Kerberos Authentication Works Keeping Your Network Secure
Authentication is the process of verifying to a sufficient degree of confidence claims about a party or message. These are the steps in Kerberos Authentication.
The Kerberos KDC returns a TGT and a session key to the PC Client.

Kerberos authentication. Basically Kerberos is a network authentication protocol that works by using secret key cryptography. Kerberos authentication takes place in a Kerberos realm an environment in which a KDC is authorized to authenticate. This request consists of the PC Client TGT and an authenticator.
A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC. Services that run on Windows operating systems can impersonate a client computer when. During authentication Kerberos stores the specific ticket for each session on the end-users device.
The Apache service was configured to authenticate user accounts using Kerberos. However it does not prevent a passive attacker from sniffing the clients encrypted timestamp message to the KDC. In Kerberos Authentication server and database is used for client authentication.
Kerberos separates authentication into two phases. The protocol was initially developed by MIT in the 1980s and was named after the mythical three-headed dog who guarded the underworld Cerberus. Using Kerberos authentication within a domain or in a forest allows the user or service access.
The benefits gained by using Kerberos for domain-based authentication are. A ticket request for the application server is sent to the Kerberos KDC. Microsoft introduced their version of Kerberos in Windows2000.
Kerberos authentication protects user credentials from hackers. It might also use NTLM which is also a provider in windows authentication. Its designed to provide secure authentication over an insecure network.
Each user and service on the network is a principal. Thus Kerberos pre-authentication can prevent the active attacker. GitLab can integrate with Kerberos as an authentication mechanism.
Kerberos is an authentication protocol for clientserver applications. If the time on a network client is more than five minutes slow or fast compared to the KDC Kerberos authentication. Kerberos was developed in the Athena Project at the Massachusetts Institute of Technology MIT.
You need to change the domain information to reflect your Network environment. To mitigate this problem it is recommended that the users use lengthy passwords. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC.
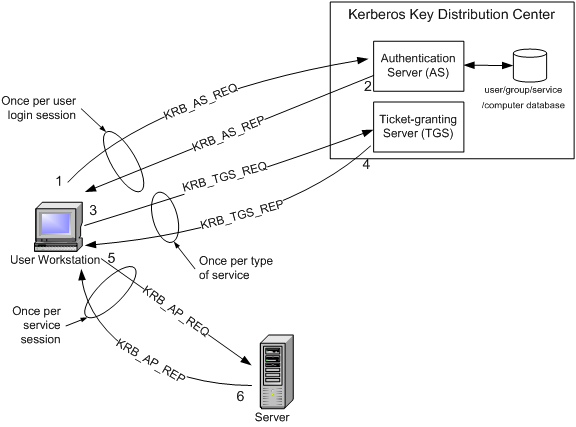
As such all clients that are running the Kerberos client must synchronize their time settings with a common time server. PC Client logs on the domain. Kerberos is a secure method for authenticating a request for a service in a computer network.
Clients authenticate with a Key Distribution Center and get temporary keys to access locations on the network. Kerberos authentication relies on timestamps to function properly. The Apache server was configured to request password authentication to access the directory named TEST.
Initial authentication takes place. Lets see how all of this works. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users.
Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. Read on to learn what Kerberos authentication is and how it protects both end-users and systems.
Typically a network application needs to know some attributes such as the name about the party sending it messages. Instead of a password a Kerberos-aware service looks for this ticket. If the attacker can sniff that full packet he can brute force it offline.
This allows for strong and secure authentication without transmitting passwords. This protocol keeps passwords away from insecure networks at all times even during user verification. Kerberos at its simplest is an authentication protocol for clientserver applications.
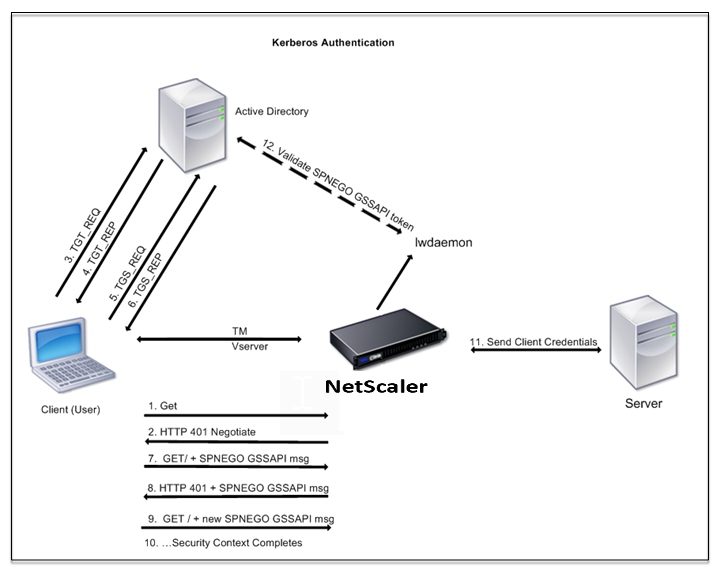
How Citrix Adc Implements Kerberos For Client Authentication

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
Intel Amt Sdk Implementation And Reference Guide
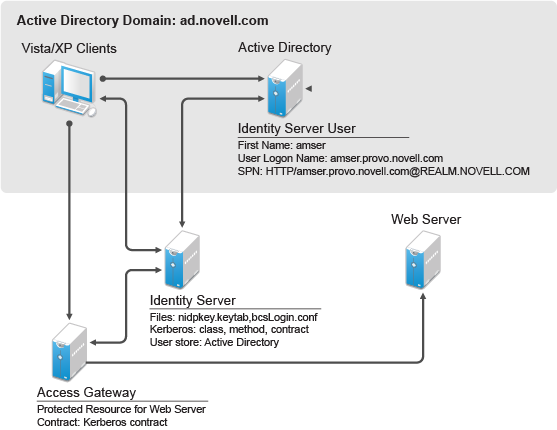
Kerberos Authentication Access Manager 4 5 Administration Guide
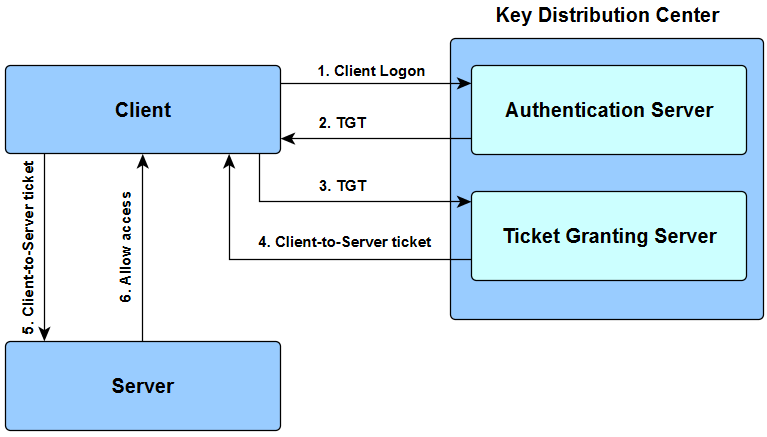
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security
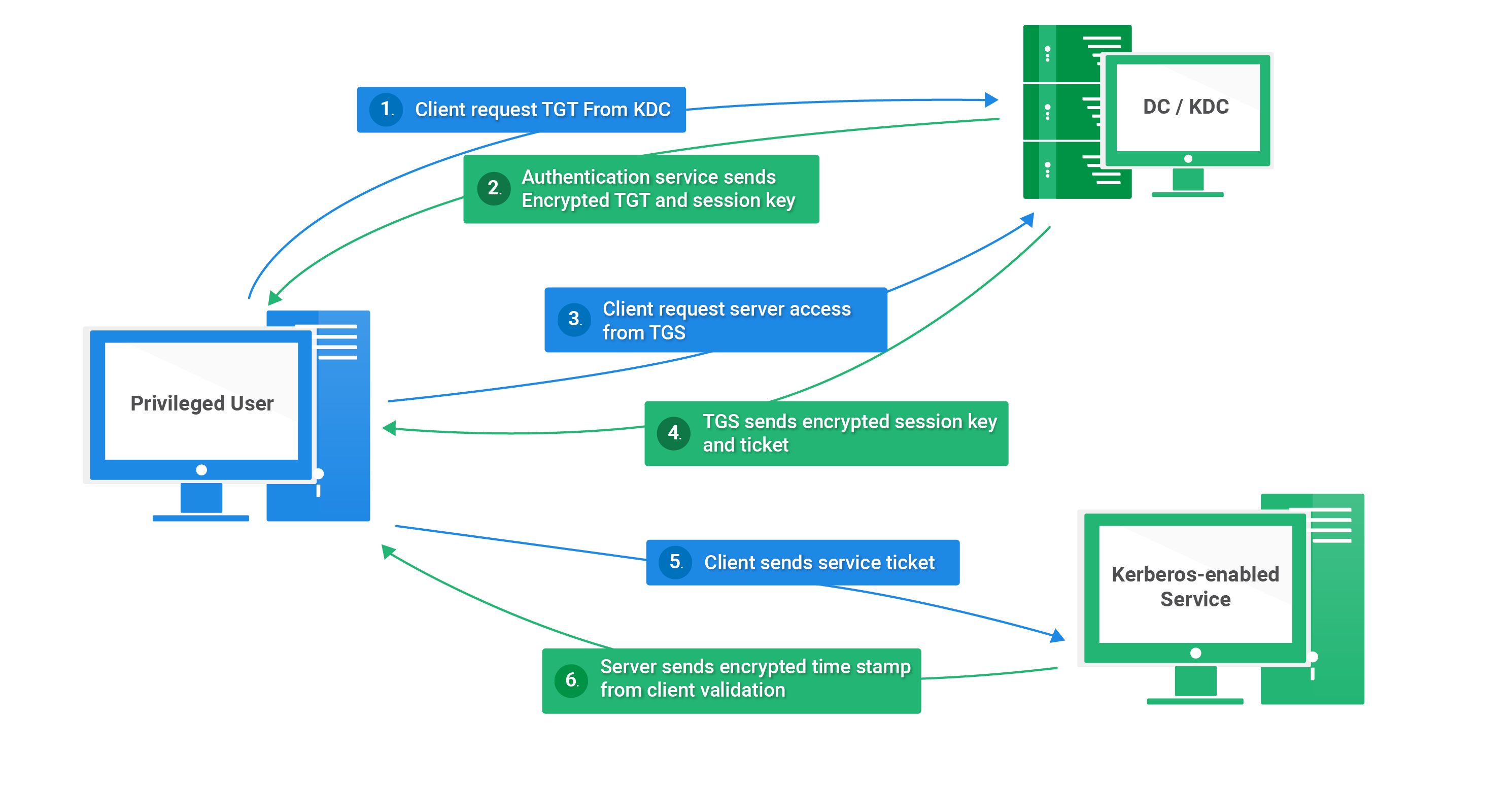
Kerberos Fundamentals What It Is And How It Works Qomplx

How Kerberos Authentication Works

Kerberos Authentication Axway Open Documentation
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community

Kerberos Authentication Explained

Windows Event Id 4768 A Kerberos Authentication Ticket Was Requested Adaudit Plus

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram

How Kerberos Authentication Works
Ken Schaefer Iis And Kerberos Part 1 What Is Kerberos And How Does It Work

Kerberos Authentication What It Is How It Works Bmc Software Blogs
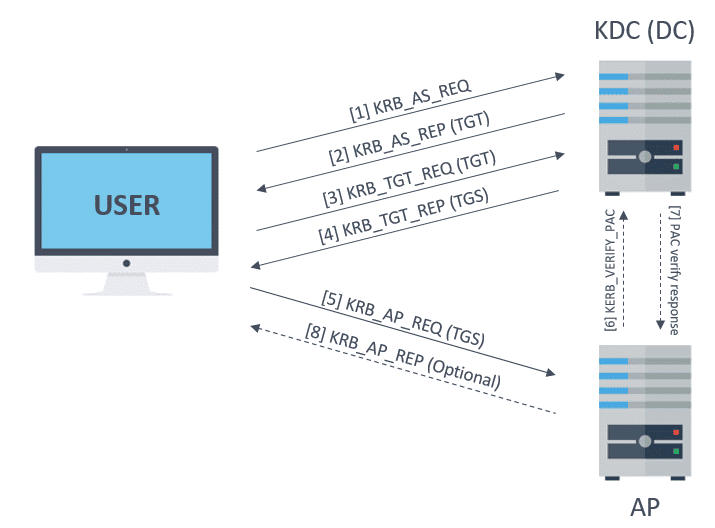
Kerberos I How Does Kerberos Work Theory

How Kerberos Authentication Works Keeping Your Network Secure
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
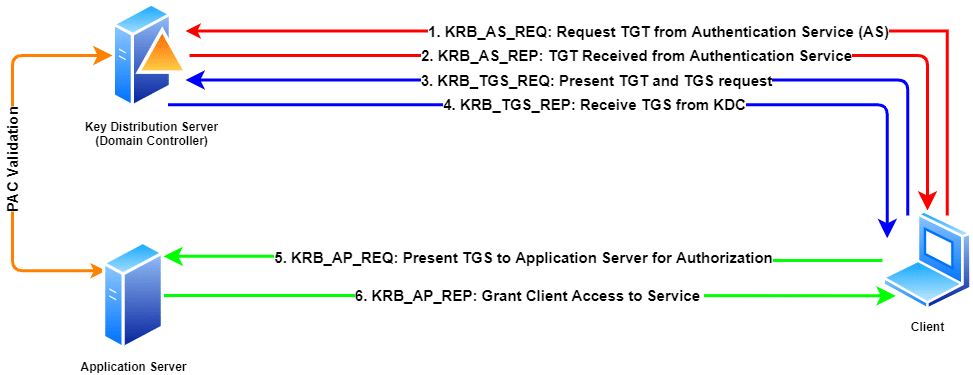
What Is Kerberos Understanding Kerberos What Is It How Does It Work